Mass vendor screening
Mass Vendor Screening (MVS) is a complex analysis of numerous client’s vendors and employees to identify red flags of fraud, conflict of interest, corruption and other issues. It is accomplished as sophisticated “Big Data” mining with the scope, which may cover hundreds and thousands of entities. It is a powerful tool that can be utilized in overall compliance and anti-fraud-related efforts. Normally, MVS is performed as part of internal fraud or regulatory compliance investigations or could be used as initial diagnostic tool in fraud risks assessment to identify potential issues in procurement/sales/business processes or reveal facts of interactions with mala fide and unreliable vendors.
A client may be interested in mass vendor screening in many cases such as:
- Evolving FCPA/UK Bribery Act risks and hardening of sanctions policy with respect to vendors/distributors in Russia;
- Newly appointed CEO/management team starts assessment of the company’s vendors, seeking conflict of interest/price escalation/assets siphoning issues to increase efficiency and work out “change plan”
- Shareholders/Board initiated internal investigation against the company’s management, seeking brief analysis of prevailing business practices and assessment of vendor affiliations;
- International/global company is concerned about alleged rumors/whistleblower reports on informal practices in its regional subsidiaries/representative offices/distributing network;
- Fictitious sales/shell companies suspected/involved;
- A high risk operating subsidiary is identified prior to M&A;
- Pending investigation or in-depth due diligence/FCPA risk audit;
- General assessment of fraud risk vulnerability of a company is required;
- A company plans Initial Public Offering, etc.
In MVS procedure, our consultants collect authorized data from a client, pick up relevant data from public and pay-for-access data sources and create structured project database for testing of:
- Potential conflict of interest/affiliations (direct or implicit);
- Unreliable/mala fide entities;
- Interconnected/affiliated vendors (tandem);
- Connections (including historic) between shareholders & directors, client’s employees, PEPs (politically exposed persons), sanctions lists and other entities of concern.
In general, analysis is of four stages:
1. Acquisition of data from a client (list of vendors, list of current/former employees, turnover with vendors, internal black lists, investigated entities, etc.).
2. Acquisition of publicly available data (United State Registry of Legal Entities, United State Registry for Individual Entrepreneurs, including historic data), public procurement platforms, stop-lists, sanctions lists, public information on PEPs, etc.) and pay-for-access data sources (SPARK Interfax, Integrum, Prima-Inform).
3. Building project database and starting data mining and testing. Also, we run various data quality improvement procedures to enhance its integrity (i.e. removal of duplicates, identification of identical addresses and phone numbers, common surnames, spheres of vendor activity, relatives and friends. The depth of our analysis is extensive; however, based on practical value of identified links and standard procedure, we limited it to extension of three entities between screened ones:
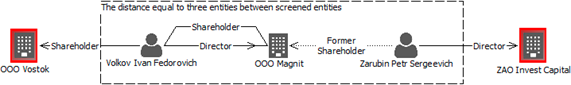
4. Reporting on findings. We report by way of a visual risk mapping with summary of the risks identified, which enable managers to spend less time on understanding of risk exposures:
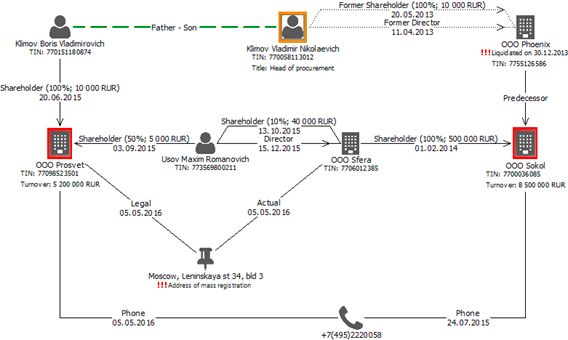
We believe that MVS together with comprehensive analysis of corporate Big data in search of fraud and other risks pursue much bigger goal. It is not so much about well-deserved punishment of a fraudster or erasing of particular scheming, it is more about efficient model of production/business process. In this sense, fraud risks assessment (and mass vendor screening as one of its tools) is a drastic undertaking for modernization and re-engineering of business processes within your company.
